Itron Identity Service
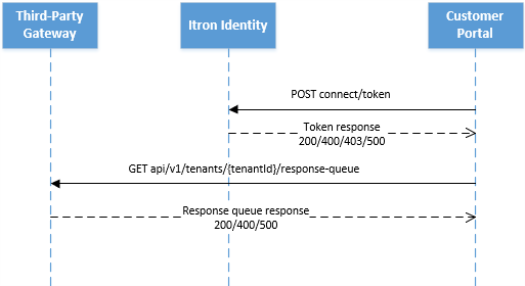
The Third-Party Gateway relays all requests to the EAC through an Azure service bus. The EAC uses another Azure service bus for relaying responses back to the customer portal. To use the Azure service bus, the utility's customer portal must be integrated with the Itron Identity Server, so that secure service principals can be set up. The security principal defines access policy and permissions for the user and application during sign in, and authorization during resource access.
Itron Identity's implementation is based on OpenID Connect authorization framework. This API creates the bearer token that grants the bearer access to REST resources or REST APIs.
Contact Itron Customer Support to obtain the Itron Identity client ID, client secret, and scope required to access REST resources. The client ID works like the service principal's username and the client secret works like its password to access the Third-Party Gateway APIs, while the scope identifies the sections of the APIs to which that caller has access.
The value for scope always remains as ThirdPartyGatewayApi. Itron Customer Support issues individual client IDs and client secrets.
Ping Third-Party Gateway response details | |
|---|---|
Request URL | POST https://idenserver.itrontotal.com/connect/token/ |
Request headers | ContentType: application/x-www-form-urlencoded |
Request body | client_id=<Itron supplied>&client_secret=< Itron supplied >&scope=ThirdPartyGatewayApi&grant_type=client_credentials |
Response schema | {"type": "object", "properties": {"access_token": {"type": "string", "description": "Jason Web Token" }, "expires_in": {"type": "integer", "description": "Specfies validitiy in minutes" }, "token_type": {"type": "string", "description": "Type of token, Always set as 'Bearer'" }, "scope": {"type": "string", "description": "Specifies ccope, Always set as 'ThirdPartyGatewayApi'" } } } |
Sample response | {"access_token":"eyJhbGciOiJS...", "expires_in":3600, "token_type":"Bearer", "scope":"ThirdPartyGatewayApi" } |
Sample Postman log | POST /connect/token/ HTTP/1.1 ContentType: application/x-www-form-urlencoded User-Agent: PostmanRuntime/7.26.10 Accept: */* Host: idenserver.itrontotal.com Accept-Encoding: gzip, deflate, br Connection: keep-alive Content-Type: application/x-www-form-urlencoded Content-Length: 150 client_id=<removed>&client_secret=<removed>&scope=ThirdPartyGatewayApi&grant_type=client_credentials HTTP/1.1 200 OK Date: Thu, 25 Mar 2021 07:53:12 GMT Content-Type: application/json; charset=UTF-8 {"access_token":"eyJhbGciOiJSUzI1NiIsImtpZCI6Ik9LZTJKeUx1cGVFVm1XUUg3bnowUXNnMzU4YjFXb054RkU2UEFYVlFLNWc9IiwidHlwIjoiSldUIn0.eyJuYmYiOjE2MTY2NTg3OTIsImV4cCI6MTYxNjY2MjM5MiwiaXNzIjoiaHR0cHM6Ly9pZGVuc2VydmVydGV...dLqjw","expires_in":3600,"token_type":"Bearer","scope":"ThirdPartyGatewayApi"} |